Extracting secured chip source code is a highly specialized and technically advanced process that involves accessing and recovering data from encrypted, locked, or otherwise protected microcontrollers (MCUs), microprocessors, or integrated chips. These devices often store critical firmware, configuration files, or operational data in binary or hex format within internal EEPROM or flash memory. The challenge lies in bypassing or breaking the security features implemented to prevent such access.
In secure systems, the firmware is typically encrypted and stored in locked memory sectors to prevent reverse engineering or unauthorized duplication. However, through sophisticated attack methods—such as glitching, fault injection, side-channel analysis, or decapsulation—it is possible to gain partial or full access to the memory contents. Once accessed, the binary can be dumped and decoded into readable formats for analysis or replication.
When extract code from Chip, there may be some experiments need to carry out, for example, through the measurement of chip surface laser scanning result can generate the photon current to establish a piece of activated area descriptive drawing when extract chip code.
Place the chip onto the electrical automation platform with 0.1 micron to extract code and we can see the great current generated from the activated area, but most of them have been covered by the metal layer and laser fail to penetrate, so these areas can’t generate any current when extract chip code from them.
The next experiment is working on the operating chip, since the chip has been programmed, chip extractor can load any value into the RAM and then pause the chip operation. Scanning the chip memorizer unit with loaded code we can see the different status of chip memorizer units, if the content is “1” then the top layer is light if the content is “0” then the bottom layer is dark.

Reverse engineering plays a central role in this field. After dumping the memory or EEPROM, engineers often use disassemblers and hex editors to decrypt and interpret the program. The goal is to recover source code logic or clone the program behavior. This process allows for the copying, replicating, or even restoring of lost firmware, which is especially valuable when no backup exists or when working with legacy devices no longer supported by the original manufacturer.
In some cases, decapsulation—a physical method of removing the chip’s protective casing—is used to probe internal data pathways directly. While this is one of the more invasive methods, it can provide access to encrypted archives or locked memory blocks when all other options fail. Once access is granted, analysts can duplicate or archive the extracted data for research, emulation, or forensic purposes.
Our experiment result on the chip code extraction is quite similar to the result issued by SANDIA LABS but the process is quite different. We replace the constant current from chip with top layer scanning, and we use constant voltage to provide the power supply, like the standard power consumption analysis to measure the current if extract chip code.
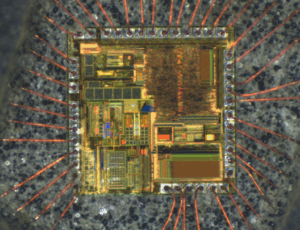
Though often associated with hacking or illegal cloning, extracting secured chip source code has legitimate applications in digital forensics, security research, industrial legacy system recovery, and competitive benchmarking. For example, recovering firmware from a damaged device or analyzing malware in embedded systems often requires breaking through locked memory.
Ultimately, the technology behind extracting binary files from secured chips is a blend of electronics, cryptography, and engineering ingenuity. Whether the goal is to decrypt a memory dump, decode a heximal archive, or reverse engineer an encrypted firmware program, each step involves precision tools and expert knowledge.

If the critical code coincidently emerge on the same location clearly on the clock cycle, then chip extractor can deduce and frozen this status, this chip code extraction method can be physically such as low temperature or other methods to pause the clock, then the chip extractor can use optical or electromagnetic probe technology to extract the code from chip. No matter for technology or facility investment can be much less then the invasive chip code extraction method.
