A binary file on a chip contains the compiled source code of a device’s operating logic—everything from basic boot instructions to complex control algorithms. These binaries are usually stored in EEPROM, flash memory, or other types of non-volatile memory within the device. When a developer loses access to the original code, or when a competitor wants to analyze a device’s behavior, the need to recover or dump the binary becomes critical.

However, most modern chips come with security features such as encryption, code protection, and read-out lock bits to prevent unauthorized access. To extract a binary file from such a locked or encrypted MCU, one must often resort to advanced techniques collectively known as chip-off attacks or hardware hacking.
One popular method is decapsulation, where the protective packaging of the chip is chemically or mechanically removed to expose the silicon die. This allows access to test points and memory interfaces. Using specialized equipment like microprobes and laser cutters, attackers can then physically attack the chip to bypass security mechanisms.
Extract MCU Binary File through read out the logic status of transistor is not a very commonly method for MCU Cracking, in order to do that, first of all we need to acquire the schematic diagram of target MCU;
Extract MCU Binary File through read out the logic status of transistor is quite normal in the invasive MCU extraction method, the traditional method of extract and read out binary file from semiconductor MCU memorizer is using mechanical probe, and the contact point is on the data bus. However, this kind of MCU cracking will refers to the direct electrical contact among the microprobe and internal circuit structure. It is a method with a lot of difficulties, from the miniature of MCU features size to use hardware access circuit on the MCU memorizer.
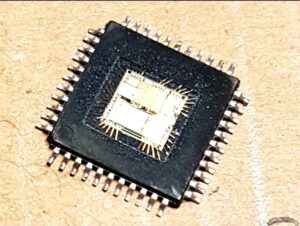
So the MCU extracter research and apply the semi-invasive MCU extract method to read out the status of the memorizer unit without bring any damage to it. But this way won’t always work and can only extract the BINARY file from CMOS SRAM which makes it unable to be prevail in the microcontroller reverse engineering market.
In the microscopy, we can use infrared concentrate on the MCU surface to analyze the SRAM. 650nm wavelength infrared is greater than silicon energy band, it will ionize internal effective area in the MCU. If the photon can reach area close to PN joint location, due to the photoemission will generate the photocurrent.
When photons enter P or N area, it will inject the free load current which can decrease the resistance in the tube. Through which we can read the status of the MCU memorizer unit and obviously the increasing current value can make the channels more smooth and can almost ignore. Direct the laser beam to the proper transistor can distinguish the two possible status.
One popular method is decapsulation, where the protective packaging of the chip is chemically or mechanically removed to expose the silicon die. This allows access to test points and memory interfaces. Using specialized equipment like microprobes and laser cutters, attackers can then physically attack the chip to bypass security mechanisms.
Once the chip is exposed, techniques such as voltage glitching, clock fault injection, or side-channel analysis (like power consumption monitoring) may be used to break or crack the security features. These techniques aim to force the chip into leaking or allowing access to the firmware or data stored internally.
Another route involves dumping the memory contents via debug interfaces such as JTAG or SWD. If these are not disabled or fused off, they can be used to copy, replicate, or even clone the firmware. In other cases, attackers may try to decrypt or decode the contents of a binary file that has been encrypted on the chip, often requiring knowledge of the underlying cryptographic implementation.

Once successfully recovered, the binary file can be analyzed using disassemblers or reverse engineering tools to reconstruct the original program logic. The extracted file, often in hex or bin format, can then be duplicated or archived for future use, whether for legitimate backup, repair, or less ethical purposes.

