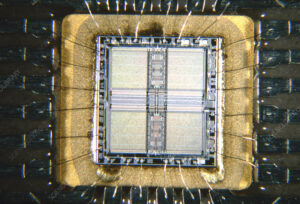
The Extract IC Protection Method refers to a range of advanced techniques used to crack the protection mechanisms of secured integrated circuits (ICs), allowing engineers or adversaries to extract vital information such as firmware, binary files, or even source code from a locked or encrypted microcontroller (MCU) or microprocessor. These methods are often applied to reverse engineer devices, perform security research, or recover data from legacy systems when no original files are available.
Modern chips are equipped with robust security features to prevent unauthorized access to memory and embedded programs. These features include encrypted EEPROMs, protected flash memory, and locked debug interfaces. However, using specialized attack strategies, it is still possible to dump, decrypt, and decode the internal contents of these protected ICs.
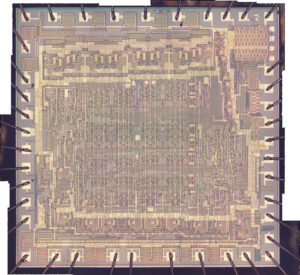
최신 칩에는 메모리 및 내장 프로그램에 대한 무단 접근을 차단하는 강력한 보안 기능이 탑재되어 있습니다. 이러한 기능에는 암호화된 EEPROM, 보호된 플래시 메모리, 그리고 잠긴 디버그 인터페이스가 포함됩니다. 그러나 특수 공격 전략을 사용하면 이러한 보호된 IC의 내부 내용을 덤프, 복호화 및 디코딩하는 것이 여전히 가능합니다.
One of the most common methods involves decapsulation—the physical removal of the chip’s packaging to expose the die. This allows direct probing of internal buses, bypassing logical security features. Once exposed, experts use techniques such as laser cutting, focused ion beam (FIB), or electron microscopy to manipulate or monitor internal signals, leading to full or partial recovery of the firmware or binary.
Another approach is to attack the chip’s bootloader or debug interface. If improperly configured or left accessible, interfaces like JTAG or SWD can be exploited to dump the contents of internal flash or EEPROM. In many cases, the challenge lies in bypassing the security bits that block external access. Side-channel attacks, such as power analysis or clock glitching, may also be used to induce faults in the system, allowing attackers to bypass authentication and copy or clone the program.
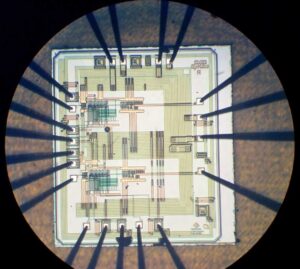
Extract IC and extract IC embedded firmware need to know the part number, this is a most important information a IC extracter should obtain in the first place. Without it, the IC extract process can’t be proceed immediately.
In order to prevent the unauthorized IC extract, some of the IC manufacturers will wipe out the marking on the TOP side of IC. But lots of IC manufacturers will print the marking on the backside of IC, such as ATMEL, and print the internal code on the backside of IC. IC extracter is very easy to infer internal code and make the proper matchment with the real part number of IC when extract IC. Some of the designer will make a further improvement on this method, they will not only wipe out the marking on the IC before extract, but also print their own marking which can make them seems more like ASIC. As we all know, extract ASIC IC could take much more cost than others, which makes only a small part of IC extracters can finally distinguish the part number of IC.
Some of the IC designer will print the new marking on the IC to prevent the IC extract. for example, there is a IC applied on the electronic game machine, the IC on the printed circuit board has been viewed as a IC to prevent extract IC with high level of security, it actually is a CPLD with lower security which has been reprinted with other markings.
From the above pictures we can see that, the marking on the top side of IC is quite similar with the ACTEL IC but only a little difference to prevent IC extracter do the related evaluation. But from the bottom side of IC, it is totally different, but its marking is quite similar to XILINX markings. This Extract IC prevention method is quite smart but has already broken the patent right law which could probably get sued by the XILINX IC manufacturer or ACTEL IC manufacturers.
Software-based methods rely on decrypting communication between the chip and peripheral components. For example, sniffing SPI or I2C traffic during startup can sometimes expose the data being loaded into memory, especially if encryption keys are not adequately protected. In certain cases, even encrypted files can be decoded using brute-force or dictionary attacks if the underlying encryption is weak or poorly implemented.
Once access is obtained, engineers can replicate, duplicate, or archive the entire chip’s content, enabling the creation of clones or emulated environments. This is especially valuable when dealing with obsolete hardware for which no documentation or original source is available.
Despite its controversial nature, the Extract IC Protection Method plays a crucial role in fields like cybersecurity research, legacy system maintenance, and competitive analysis. However, it also raises ethical and legal questions, especially when used to hack or break proprietary systems without authorization. Developers are therefore encouraged to implement multiple layers of defense to protect secured MCUs, including strong encryption, tamper detection, and disabling debug ports in production.
In summary, the art of extracting data from protected chips is a complex mix of hardware manipulation, software exploitation, and deep technical knowledge. Whether to recover a lost program or to understand how a microcontroller works, these techniques remain at the heart of modern IC reverse engineering.