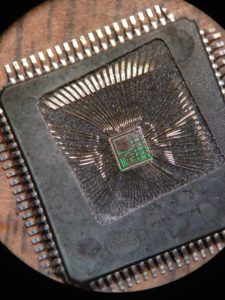
Extract Chip Embedded Firmware
Extracting chip embedded firmware is a complex process that involves accessing the secured data stored within a microcontroller (MCU) or microprocessor. Whether for reverse engineering,

Extracting chip embedded firmware is a complex process that involves accessing the secured data stored within a microcontroller (MCU) or microprocessor. Whether for reverse engineering,
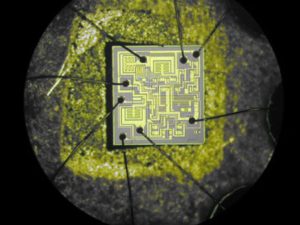
In the world of embedded systems and hardware reverse engineering, the ability to extract chip firmware is critical for various legitimate purposes, such as system
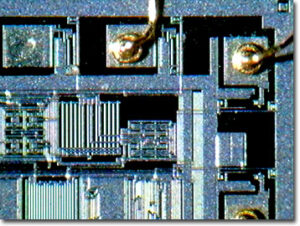
Extract Microcontroller AT89C55 Code starts from crack protective ATMEL MCU AT89C55 fuse bit and restore embedded firmware in the format of binary file or heximal
Extract MCU AT89C52 heximal data and binary file from secured flash memory and eeprom memory, original secured AT89C52 microcontroller tamper resistance system will be disabled
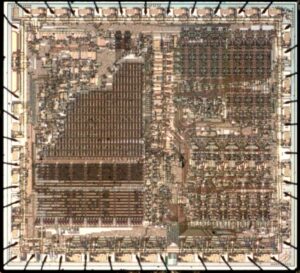
Extract IC AT89C51 binary needs to reverse engineering ATMEL AT89C51 secured microcontroller protection and decrypt AT89C51 MCU microchip’s fuse bit, dump embedded firmware in the
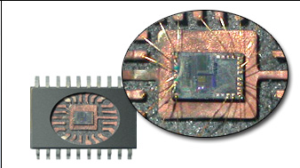
Chip extract technology has become prevail on the very old and low protection series of microcontrollers. In order to prevent the intellectual property being stolen

Modern hardware often relies on secured, locked, and encrypted microcontrollers (MCUs) and microprocessors to protect critical firmware, source code, or EEPROM data. However, advanced techniques
Extract microcontroller embedded firmware include the ultra-violet radiation extract, this is a microcontroller extracting method which has been applied on a great many of microcontrollers
