Modern microcontrollers (MCUs) often come with secured or encrypted firmware to prevent unauthorized access. However, there are situations where engineers need to extract microcontroller source code for recovery, debugging, or legacy system maintenance. This article explores various techniques used to break, decrypt, or replicate protected firmware from chips.
Common Techniques to Attack MCU Source Code Protection
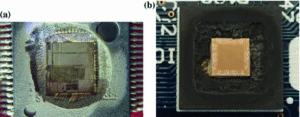
1. Decapsulate and Probe the Chip
Some attackers decapsulate the MCU to expose the silicon die. Using advanced tools like Focused Ion Beam (FIB) or microprobing, they can dump the binary directly from the memory or EEPROM/Flash. This method bypasses locked readout protections but requires specialized equipment.
2. Side-Channel Attacks to Decrypt Firmware
By analyzing power consumption, electromagnetic leaks, or timing variations, hackers can crack encrypted firmware. Differential Power Analysis (DPA) and Fault Injection are common ways to decode secured programs without triggering security mechanisms.
3. Exploiting Debug Interfaces to Recover Code
Many MCUs have JTAG, SWD, or UART interfaces left unprotected. Attackers can hack these ports to copy or dump the source code. If the debug mode is disabled, voltage glitching can sometimes bypass the lock.

4. Brute-Force and Reverse Engineering
For weakly protected chips, brute-forcing the memory can reveal the archive structure. Once extracted, disassemblers and decompilers help replicate the original logic.
5. Microprobing to Clone Firmware
Invasive methods involve removing the chip’s packaging and using microprobes to read the binary directly from the microprocessor. This allows attackers to duplicate the file even if the firmware is secured.
Extract Microcontroller Source Code from program memory and data memory, reset the MCU Protection by attack MCU security fuse bit;
Extract microprocessor’s embedded memory can use the simulated faulty injection to break MCU firmware. As we all confess, focus ion beam can use to modify the status of SRAM unit.
And this process can also be stimulated by DIODE-2D software. Model reveal that the main cause of reversor status modification affected by the laser is locked effect on the parasite circuit result from radiation.
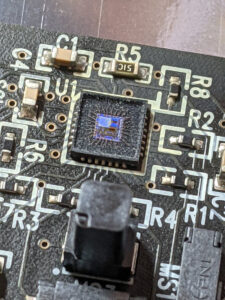
The status of reversor will only change when the required laser strength lower than the internal parasite structure threshold value. It is the best situation to turn around the laser focusing point when approaching the transistor channel area, but the locked effect can’t be eliminated, since the ion pair generated from laser will fill the reversor swiftly and cause the increase of currency in all of the internal PN conjunctions.

