When a chip manufacturer locks, encrypts, or otherwise secures a chip’s memory, it becomes difficult—by design—to read, replicate, or clone the embedded program. However, experts in hardware reverse engineering have developed methods to crack or break through these protections. The goal is to gain access to the binary file, which may contain the full firmware, source code, or other mission-critical program data.
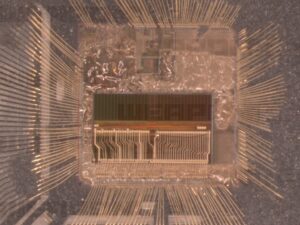
The first step in many extraction operations is to decapsulate the chip. This physical process involves removing the chip’s outer casing using acid or mechanical means to expose the silicon die. Once exposed, high-powered microscopes and imaging techniques are used to locate the memory regions. In many cases, decoding the structure of the memory is a prerequisite before attempting any direct extraction.
Next, attackers often use techniques like voltage glitching, laser fault injection, or side-channel analysis to bypass security features. These advanced hardware attacks exploit vulnerabilities in the chip’s design to gain unauthorized access to memory. For example, a laser can disrupt specific parts of a secured MCU’s boot routine, momentarily disabling the protection mechanism and allowing the memory to be dumped.
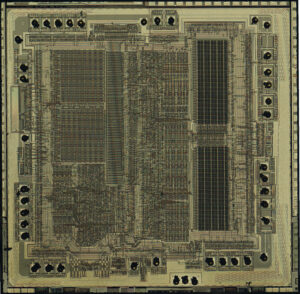
Once access is granted, specialized tools such as chip readers, oscilloscopes, and signal decoders are employed to decrypt or decode the binary file. If the data is stored in an encrypted archive or protected flash segment, cryptographic analysis and brute-force attacks may be necessary to fully recover readable firmware.
Extracting the IC binary is not just about copying bits—it’s about replicating the exact functionality of a protected system. In industries such as aerospace, automotive, and medical technology, cloning a chip may allow for hardware repair, program restoration, or even unauthorized duplication. While some see it as a valuable means of legacy system maintenance or cybersecurity research, others consider it an act of industrial espionage or digital piracy.
Extract IC binary can be separated into several different methods, they are include invasive microcontroller unlocking method, which has the highest cost and spending; non-invasive IC breaking method which is the cheapest method to extract IC binary, the final step also the most prevail method is semi-invasive mcu cracking method.
IC ikilisini çıkarmak birkaç farklı yönteme ayrılabilir, bunlar arasında en yüksek maliyete ve harcamaya sahip olan invaziv mikrodenetleyici kilidini açma yöntemi; IC ikilisini çıkarmak için en ucuz yöntem olan invaziv olmayan IC kırma yöntemi ve son adım da en yaygın yöntem olan yarı invaziv mcu kırma yöntemi bulunur.
Ultra-violet radiation extract is a very useful way, and in order to prevent this method, all of the microcontroller IC which base upon the EEPROM will design a metal layer which can’t penetrate the ultra-violet radiation to cover the security fuse. For example, most of the 14 bits and 16 bits core PIC microcontroller has possessed this design.
It can not only protect the security fuse to be reset, and also make it very difficult to locate it security fuse through which can prevent IC code extraction effectively by ultra-violet radiation. Until recently, the faulty injection has been introduced, nowadays, there are two ways to extract IC against this protection, one of them is by using laser cutting or Focus Ion Beam, remove the top metal protective layer through reverse engineering technique.
Another way is increase the top metal layer, and use inverse memorizer unit which makes the ultra-violet radiation become more slow. For instance, AT89C51 microcontroller IC from ATMEL, its protection mechanism will make it security fuse can’t be reset once the wipe out operation proceed. However, if ultra-violet radiation can swift the security fuse from unsecure status to secure status, this characteristic can be used to locate the security fuse. In order to avoid this point, some of the microcontroller IC can use dual inverse security fuse and top metal layer protection, for example, PIC16F628 and PIC16F876 from MICROCHIP.
In summary, to extract IC binary from a locked or encrypted chip is a complex endeavor requiring a deep understanding of both physical and digital security. Techniques used to hack or break into a microcontroller or secured memory system are constantly evolving in response to ever-tighter security mechanisms. Whether for ethical research or nefarious purposes, the ability to decode, copy, or replicate protected firmware remains a powerful and controversial capability in the world of hardware security.
