In the world of embedded systems and hardware reverse engineering, the ability to extract chip firmware is critical for various legitimate purposes, such as system recovery, product analysis, or security research. Firmware, often stored in flash memory, EEPROM, or embedded MCU/microcontroller/microprocessor memory, holds the low-level control code that governs how a device operates. Extracting this firmware can uncover critical source code, binary routines, or configuration data needed for debugging or understanding device behavior.
However, most modern chips come with protected, locked, or encrypted firmware to prevent unauthorized access. These secured systems often require advanced techniques to dump, decode, or decrypt the embedded program. Security researchers and engineers often employ methods to crack, break, or attack the chip’s defenses, especially when traditional debugging interfaces like JTAG or SWD are disabled.
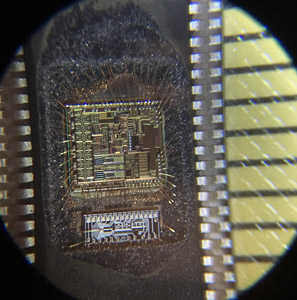
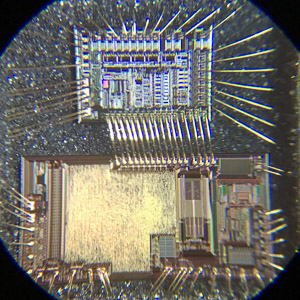
One of the most aggressive but effective techniques is to decapsulate the chip, removing the protective packaging to access the silicon die directly. This physical access may allow the use of microprobing to read the firmware memory or extract stored archives of program files. While invasive, this method has been used to recover firmware from locked or encrypted devices that have no alternative method of access.
Other techniques include fault injection attacks, such as voltage glitching or clock manipulation, to momentarily bypass security mechanisms and dump the memory. Once acquired, the firmware can be analyzed, cloned, replicated, or even duplicated to recreate the device’s original behavior or build compatible systems. In some cases, the extracted code is decoded and decrypted to reveal readable source code or configuration files.
While these techniques are powerful, they raise ethical and legal questions. It is crucial to understand that firmware extraction must comply with local laws and intellectual property rights. Many companies implement strong encryption and hardware-level defenses to prevent firmware copying, protecting their data and intellectual property from being hacked or reverse-engineered.
In conclusion, to extract chip firmware from a secured or protected device involves a combination of hardware and software expertise. Whether the goal is to recover, analyze, or replicate embedded systems, understanding the underlying memory structure and protection mechanisms is key to success.
Extract Chip Firmware can help to bring a 100% clone of firmware out from IC chip. Advanced Imaging Technology can also be the semi-invasive chip firmware extract skill. Include the infrared radiation, laser scanning and thermal imaging. Some of them can be used on the rear side of chip extract, it is very impactful on the modern chip which has the multilayer metal design. Some of these technologies can even observe the individual transistor inside chip.

The flaw defect of Semi-invasive chip extract can modify the content inside SRAM, OR change the status of each transistor inside a chip when extract, this can almost control the operation of chip limitlessly or use any kind of protection mechanism.
Compare with the un-invasive chip content extract, semi-invasive need to decapsulate the external package of chip. But the facility can be much cheaper than the complete invasive chip extract. And can complete the extract within a short period of time. Meanwhile, it can be minimize to the certain scope, sufficient skill and knowledge can contribute to the chip software extract swiftly and simple.
There is some operation when chip dump extract, such as searching security fuse, can be performed and executed automatically. Compare with invasive chip archive extract, semi one doesn’t require precise location, it will normally have effect on the transistor of all or part of area.
